Despite the nature of the globally connected internet, international law has not kept up with the rise in cybercrime and threat actors can often operate without fear of consequences. Threat actors vary widely and they are geographically located across the globe.
Who are “Threat Actors”?
- Internal threats: Some bad actors are internal to the organization. Typically, these attackers are more opportunistic operating on their own.
- Cybercriminal organizations: Other attacks are part of a coordinated effort within a hacking group. The recent Colonial Pipeline ransomware attack for example, was orchestrated by a cybercriminal organization.
- State-sponsored attacks: Others attacks are state sponsored efforts through countries like North Korea. It is believed their cyber actions are one of the top revenue producing sources for their government.
4 Main Functions of Attacks
- Money/financial gain: Ransom and extortion are most common
- Future and further attacks that tie back to #1
- Espionage/corporate gain
- Reacting to events (like natural disasters) to mainly obtain #1 reason of financial gain
Financial Losses from Phishing Attacks
Since 2005, individuals have lost an estimated $929 million and organizations have lost roughly $2B/year due to phishing attacks.
Most cybercriminals act like a business, evaluating ROI (time vs payoff). Recently, there has been a significant decrease in the value of account logins such as access to social media profiles or PayPal accounts. This decrease has forced cybercriminals to produce new revenue streams.
The Birth of Ransomware and Extortion
Cybercriminals have evolved. They’ve shifted their focus away from account credentials in favor of ransomware – an easy, lucrative method of coercing victims to pay ransom for their data. As more and more companies work to avoid paying ransom, extortion has become the new norm.
These extortion threats are typically positioned as “pay us now or we will post your data online publicly”. Extortion efforts have even spread into other aspects of social engineering such as “pay me or I will post pictures or send pictures to someone, etc.”
Types of Social Engineering
- Phishing
- Spear Phishing
- Voice Phishing (Vishing)
- SMS Phishing (Smishing)
- Business Email Comprise
- Loss of Credentials/Password Leaks
Innovative 2020-2021 Trends
- Pointing email links to Google search results that direct to attacker-controlled malware laden websites.
- Pointing email links to non-existent pages on an attacker-controlled website that mimics real sites (Gmail, O365, and Facebook).
- Spoofing company specific O365 sign-in pages to look real to trick users into providing their credentials.
- It’s not just email anymore, text and voice phishing are on a dramatic rise in 2020 and 2021.
Below are two examples of phishing attacks that illustrate these types of attacks.
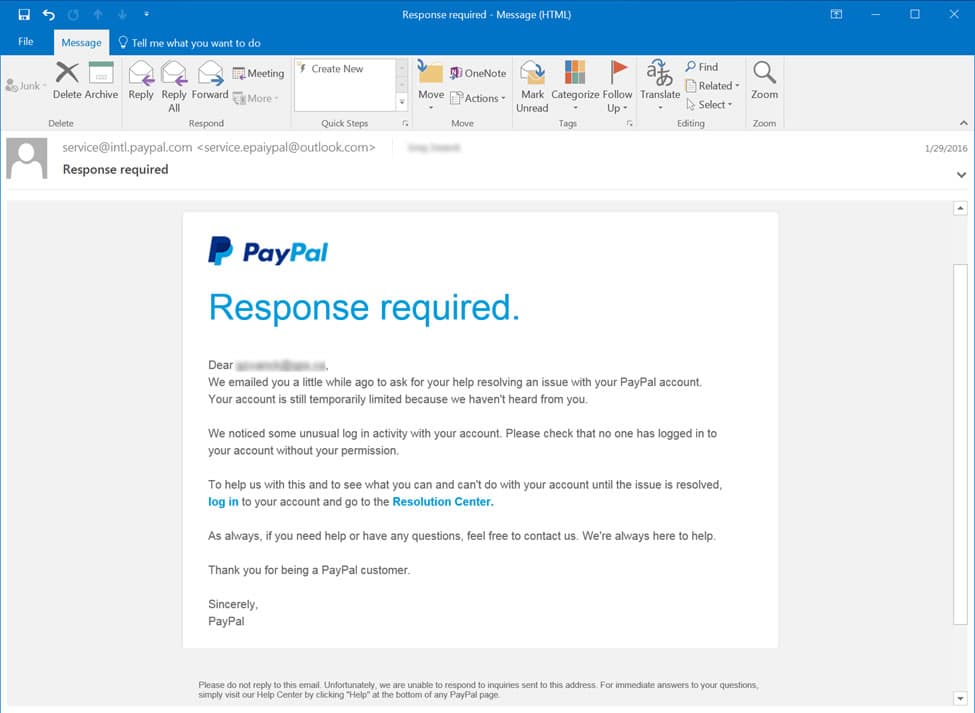
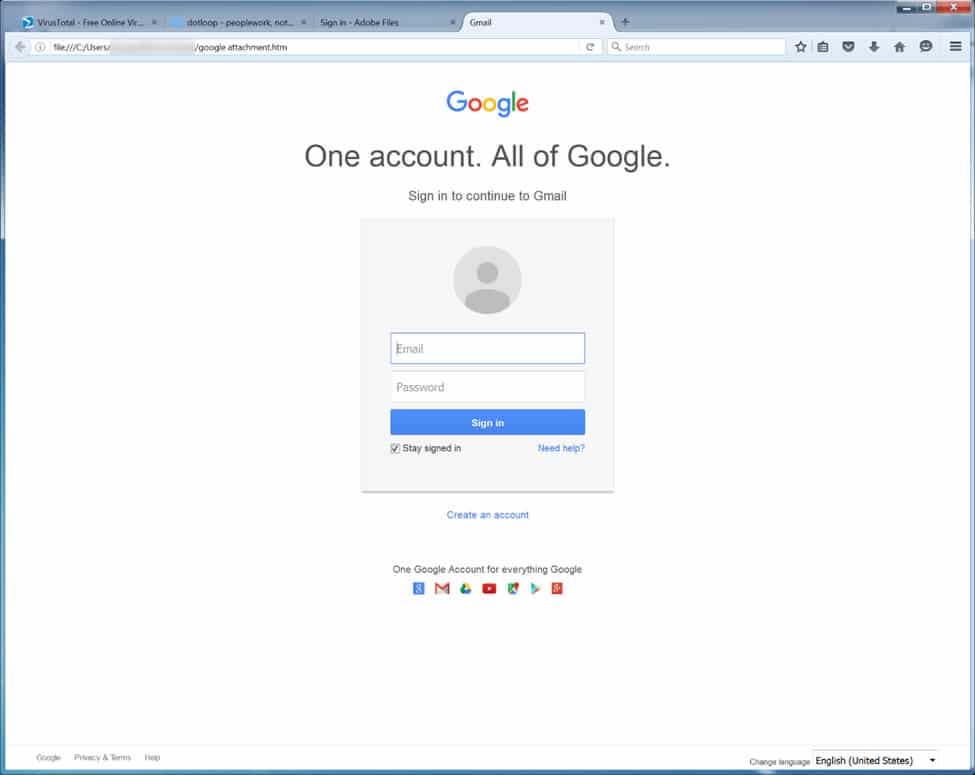
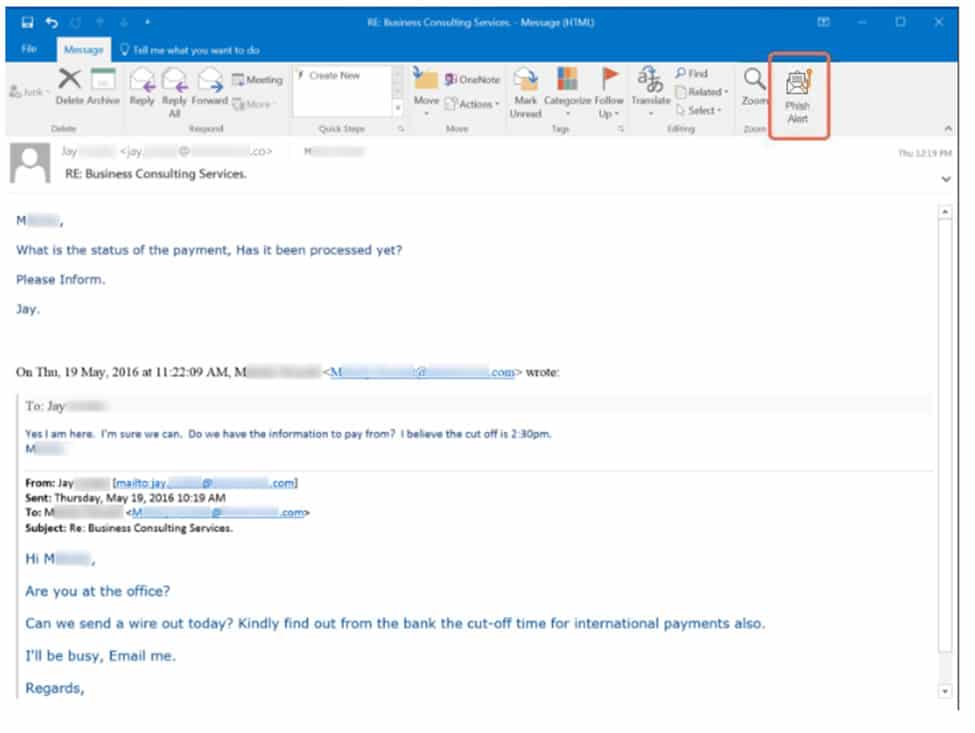
A secondary type of phishing is known as a spear phishing attack. The term spear phishing is meant to signify going after a higher value target such as a business owner or executive. Attacks that impersonate a senior level employee or owner are 75% more likely to successful. Credit Card scams are very common for this.
[ss_click_to_tweet content=”Attacks that impersonate a senior level employee or owner are 75% more likely to successful.” style=”2″]Below is an example of a spear phishing attack targeted at an executive.
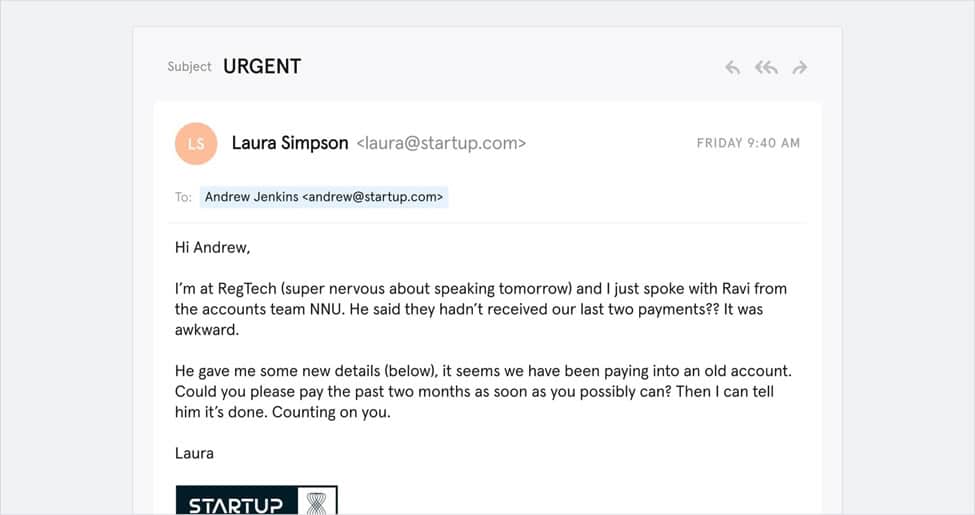
Business Email Compromises (BECs)
Business email compromises are the new and rising trend in 2021. The reason for this growing trend is the success of these attacks.
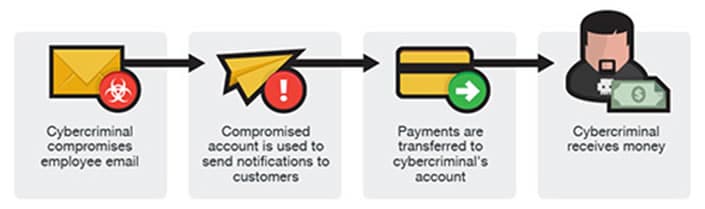
Through phishing, hackers take control of an existing communication/chain to social engineer a user to take action. It begins with a successful phishing attempt such as the examples above and below. Once a bad actor has access to a user’s mailbox, they use that legitimate mailbox to attempt to commit fraud or attack other targets.
Common Themes
- There is almost always an attempt to wire funds in these scenarios. Sometimes the spear phishing attempt may be to obtain gift cards, but no matter what the end goal is to obtain money.
- These are very difficult for end users to spot due to hackers using legitimate email accounts and an existing email chain with a user they recognize within the organization.
- Spoofing is still prevalent in this dynamic, but it is becoming less and less used due to the ease of compromising an account.
Innovative 2020/2021 Trends
- Business email compromises were the #1 vector for loss in 2020 and higher usage has been seen in 2021 than ever before.
- Once a threat actor has access to an email account, they wait and learn. They work to pick up mannerisms, language choice, etc. so that when they start executing attacks, their success rate is higher.
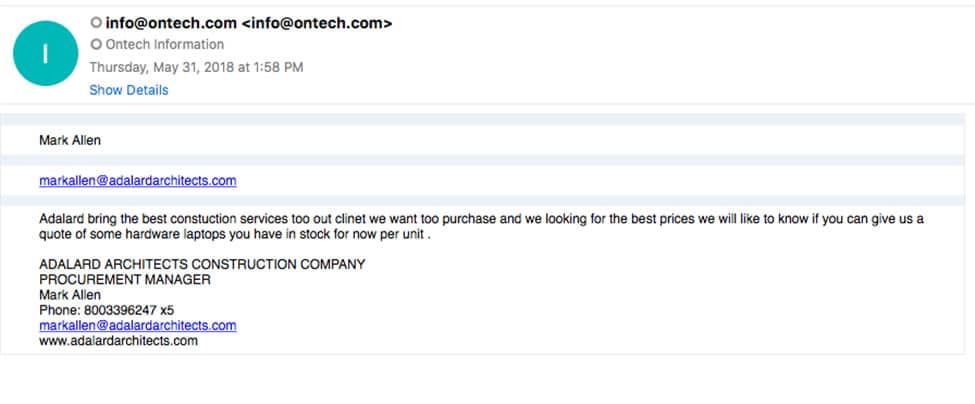
Below is a phishing example that Ontech experienced. The sender was real person, with a LinkedIn profile and everything to match. However it was all fake, – the website, the person, etc. The goal of this attack was to see if Ontech would ship hardware to them without payment. If Ontech would have shipped the hardware, our organization would have lost thousands of dollars.
Real-World Examples of Successful Social Engineering Attacks
2021: A Wisconsin Municipality
- A contractor’s email was compromised.
- The threat actor replied to an active email chain in regards to a construction project and requested payment.
- A member of the municipality executed payment at the direction of emails from the contractor.
- It turned out that the wire information provided was not for the contractor, but the cybercriminal.
2021: An Ontech Client
- An accounting user’s mailbox was compromised. The threat actors watched the account for roughly 6 months before taking any action.
- The accounting user and owner communicated about their upcoming vacations, both were set to be out for a week. The owner was going to be without access to phone/email for most of the time.
- On the second day of their vacations, the threat actor started their attack by emailing customers about a change in banking info with new wire/ACH payment forms and created rules in outlook to hide all their communications.
- The cyber criminals worked with customers to update their information and attempted to mask changes by asking for updated W9s, COI, etc. as part of an accounting conversion.
Preventing the Loss of Credentials
Credentials can be obtained through phishing, password reuse from hacked sites, or by making them too easy. The above scenarios might have been prevented if all parties involved followed password best practices and their respective organizations participated in security awareness training.
While you can’t control breaches that occur on behalf of vendors/services, you can control the passwords you chose. Unfortunately, it is still all too common for users to reuse passwords. Once a website is compromised and the data is leaked, threat actors you’re your username/email and use it to log into other systems.
In fact, the number of attacks/breaches that happen as a result of password reuse is estimated to be above 50%!
[ss_click_to_tweet content=”The number of attacks/breaches that happen as a result of password reuse is estimated to be above 50%.” style=”2″]Most users don’t realize that a password has been compromised until it’s too late – you must react quickly if you see a website is hacked where you hold an account.
Known Recent Breaches of Information Exposure
- Facebook: April 2021 – 533M users
- Facebook: March 2019 – 600M Users
- Facebook: April 2019 – 540M
- Microsoft Email Services: April 2019 – Unknown Count
- Quest Diagnostics: June 2019 – 12M
- Capitol One: July 2019 – 100M
- Various Online Betting Sites: Jan 2019 – 108M Users
- Houzz: Jan 2019 – 40M Users
- Dunkin Donuts: Feb 2019 10M Users
Avoid Becoming a Victim: Helpful Phishing Resources
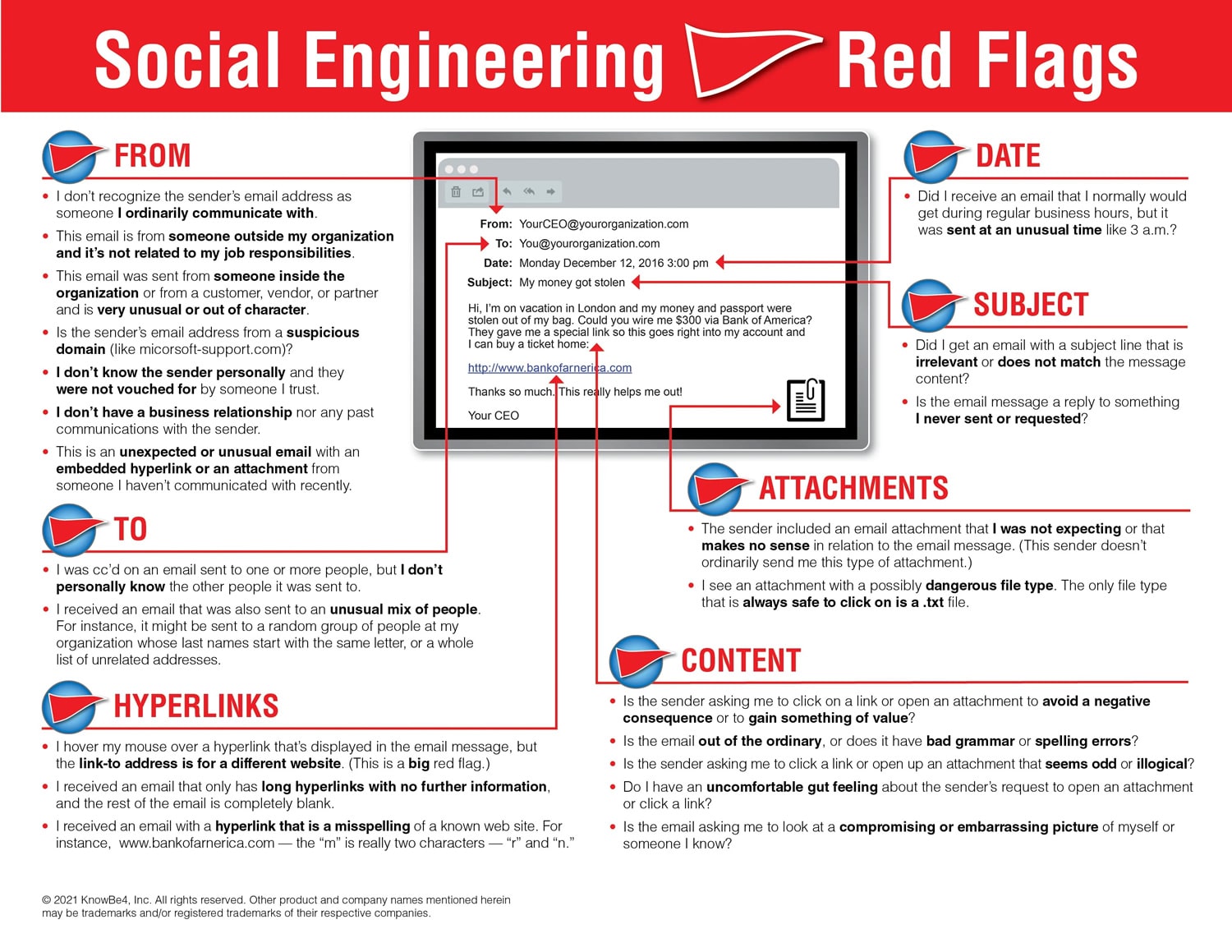
- Review social engineering red flags to look for before you take any finance oriented action based on an email. Courtesy of https://www.knowbe4.com
- Take the test – are you likely to be a phishing victim?
- 10 Ways to Avoid Phishing Scams
- Take a Free Dark Web Scan to see if your credentials have been compromised.
Ontech encourages you to take steps toward educating users and strengthening your overall network security. Request a complementary free network discovery and our professional technicians will identify high risk vulnerabilities within your business and make recommendations to strengthen the security of your network – from data backup, to firewalls, server security and more. Or, call our support team at 262-522-8560 with security or IT questions anytime!